eDiscovery Explained
The Ultimate Guide
What is eDiscovery?
- Discovery: The initial phase of a lawsuit where both parties exchange relevant information.
- eDiscovery (Electronic Discovery): The process of collecting, securing, and making electronically stored information (ESI) searchable for legal review.
- Purpose: eDiscovery ensures digital evidence can be used in civil lawsuits (not criminal cases).
- Scope: Starts when a lawsuit is foreseeable and continues until digital evidence is presented in trial.
- Key Steps: Collecting, preserving, reviewing, and producing digital evidence.

Identification
Determining what data is required, who the custodians are (who has control over it) and where the data located.

Collection
Copying the data into a secure repository.

Production
Producing the information to the other party.

Preservation
Ensuring the identified data is not deleted or modified.

Processing, Review & Analysis
Reducing the collected data set down to relevant information.


Presentation
Presenting the information during trial.


Types of Electronically Stored Information (ESI)
Here’s some examples of data that could be identified as containing relevant information: Emails, Social Media Content, Text Messages, Voicemail, Instant Messages (Skype, Viber, WhatsApp etc.), Documents, Spreadsheets, Calendar Files etc. All data from these devices is known as ESI (electronically stored information).
Sources of Electronically Stored Information (ESI)
ESI can be collected from numerous devices, such as phones, tablets, laptops, desktops and any other source that stores electronic data, including, but not limited to networked drives and online sources such as websites, apps and databases in the cloud.
Understanding Metadata in Electronic Files
Many electronic files also have associated data called “metadata”. For example, an image file may have metadata that includes when the picture was taken, where the picture was taken, the camera model, etc. Document metadata may include properties such as when the document was created, last modified, the author’s name, the time spent editing etc.
The Impact of Big Data on ESI
eDiscovery Stages
Electronic Discovery Reference Model
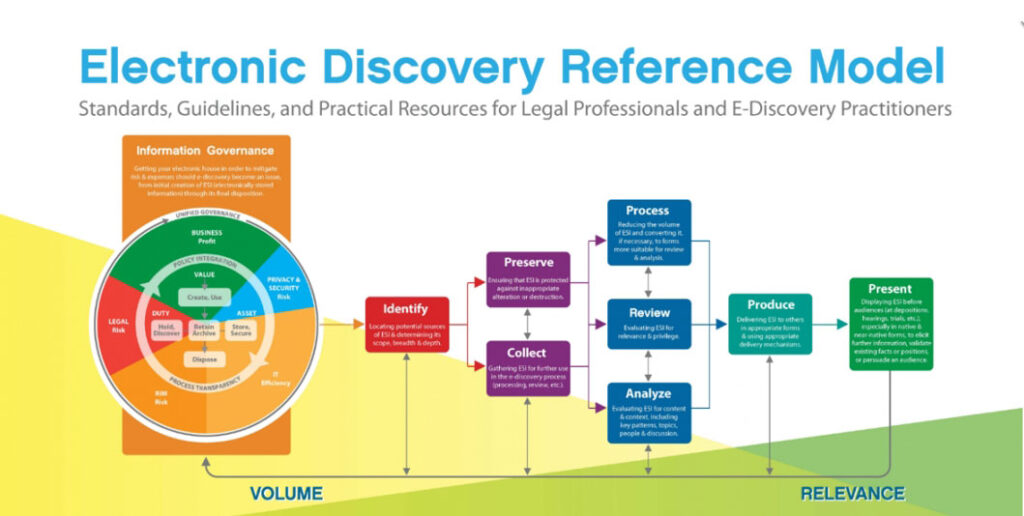
Information Governance
Information governance (IG) serves to support processes that an organization uses to maximize the value of its electronic information, while minimizing costs and risks associated with keeping that electronic information. It’s not really a step or stage in the eDiscovery process, it’s more about managing “big data” so that relevant data can be accessed quickly when needed.
Many organizations are yet to put IG into practice. That said, it is now becoming a conversation that many companies are starting to have.
Collection Strategy
Before moving through the Identification, Preservation and Collection stages, it’s beneficial to build a strategy.
How do we identify what to collect?
How do we preserve the data?
How are we going to collect it?
The best approach is to develop an e-discovery collection strategy and plan which should be unique to each matter. For example, in some cases it may be important to collect data immediately. In other cases, early collection may not be necessary (the data is already preserved).
The strategy is then used to select a collection method and execute the collection plan.
What does the e-discovery collection strategy involve?
The collection strategy can vary depending on the matter. For example:Things to consider usually include:
- Identifying the number of custodians to collect the data from. Whose data should ultimately be reviewed?
- Identifying relevant data. What’s important and what’s not?
- How will the data be preserved (prevent data spoliation)? For example, prevent the metadata changing.
- Why is the data is being collected from certain sources? It is important to consider why and how the data is being collected. Why choose one collection method over another?
- Data sources will be discussed in more depth in the next section.
- How accessible is the data (what are the data sources, and where are they located)?
- Are any special tools needed to collect the data?
- Is there any sensitive or encrypted data that warrants special measures?
- Who will be involved in the collection process (cross-functional team – legal, IT, experts)?
- Are there internal resources to help with the data collection?
- What is required to collect the data legally (litigation hold notice)?
- Which collection methods will be adopted?
- Planning for a Meet-and-Confer. Here the opposing parties meet and confer at least 21 days before the scheduling conference with the court in order to work out agreements on the preservation of ESI, the forms of ESI production, the methods that will be employed to filter out irrelevant information, and the protection for privileged information. The meet and confer will make eDiscovery more efficient, help reduce discovery disputes, and most importantly, get parties to the litigation’s most relevant information faster.
- Draft an ESI Protocol. Shortly after the Meet-and-Confer, it is good practice to draft the ESI Protocol. This document is often entered by the judge as a formal order and controls the conduct of electronic discovery in the case.
The ESI protocol will contain the following information:
- the scope of the ESI collection efforts
- the format in which electronic documents will ultimately be produced
- the handling of privileged information
Identifying What to Collect
Electronic discovery begins with identifying what to data to collect for review.
What electronically stored information (ESI) may be relevant to the case?
Who are the custodians?
Identification begins as soon as a lawsuit is reasonably foreseeable.
During this stage, interviews with key players and IT staff are conducted to establish what ESI may be relevant, where the relevant discoverable data is located, how the data can be collected, any special tools required, etc.
It’s necessary to learn where potentially discoverable data resides to issue an effective legal hold.

Preservation
Once relevant electronically stored information (ESI) has been identified, it’s extremely important to ensure that the data is preserved, kept intact – not modified, corrupted or lost, the legal community refers to this as “spoliation”.
It’s important that data preservation is conducted properly, to avoid spoliation of metadata and/or files.
A legal hold is usually used to preserve ESI. A legal hold is a formal notice sent from the legal team, stating that a lawsuit is anticipated and the recipient (custodian) must preserve all ESI that may be relevant to the matter.
But it’s not only about ensuring ESI relevant to the matter is protected from spoliation, it’s also about trying to preserve only the necessary data. Preserving unnecessary data causes inefficiencies and increases costs and risk.

eDiscovery Collections
- After electronically stored information (ESI) had been identified and preserved, it must ultimately be collected and stored in a secure repository for review.
- The collection stage is often the most complex stage of eDiscovery, requiring professionals from both IT and legal to collaborate and ensure the extraction process is properly executed.
- Relevant ESI may be stored across many different types of data sources, each one requiring different collection methodologies to ensure the data is collected properly.
Here’s a list of some common data sources that ESI may need to be collected from for electronic discovery.
Archive Data
Active Data is ESI that is stored on local hard drives, network attached storage (NAS) or other networked drives. This includes emails and other traditional files that are stored on devices such as laptops, desktops, servers and network attached storage. This type of data is usually the easiest to access and collect.

Mobile Data
This category includes phones, smartphones, tablets and blackberry devices. Collecting ESI from these types of devices will generally require specialized knowledge and sophisticated tools.

Backups
ESI that has been moved to backup devices such as tape drives or disaster recovery systems. Backup systems often compress files, this makes it difficult to search and access files. Typically, the files will need to be restored first.


Cloud Data
More and more data is being stored in the cloud (remote data that is stored and accessed over the internet). This not only includes the corporation's own applications, it also includes data stored by third party service providers such as CRM and accounting software, instant messaging services (skype, slack), social media networks, storage services (Dropbox, OneDrive), etc. Accessing this type of data can be beyond the reach of internal IT and may require specialized help.

Offline Data
Offline Data is ESI that is sent to offline storage or is no longer active (no longer in use). Examples include old computers, old hard drives, portable hard drives, USB sticks, optical disks and archived data. Collection this type is data is relatively easy if the whereabouts are known.


Hidden Data
This can include deleted data, files and fragmented files. Deleted data is not visible through the regular operating system, but it may still exist. It’s possible to recover deleted data with specialized tools and/or software if the sectors have not been formatted or overwritten with new data.

Once the data sources have been established, we are able to find out how much data is involved, how accessible the data sources are, and what specialized recovery processes and tools are required.
This knowledge then helps decide which data collection methodologies are best suited.
Typical Collection Methods
Collection Service (outside service provider is engaged)
A third-party collection service, like QUiVX is used to perform the collection of ESI. These experts are likely to know the latest best practices, have all the specialized tools and follow set processes. Although it may come with increased cost, it may be worth it for organizations with little eDiscovery experience.
Processing, Review and Analysis
- After collection, it’s time to process, review and analyze the information.
- The processing part aims to reduce the dataset by removing irrelevant data.
- The review stage involves reviewing and analyzing the ESI to determine which ESI is relevant to the case. A review team is selected based on the variables of the individual case, such as the amount of data, the deadline, and the budget.
- Law firms or review service providers are usually engaged to handle the review and are typically paid by the hour. It’s the most expensive stage of the e-discovery process, accounting for about 75% of the total e-discovery cost.
- A deep understanding of the case is necessary for an effective review, the reviewers need to know what to search and look for.
- The review stage is obviously extremely important, it’s when the law firm gain a greater understanding about the case, helping them to develop a legal strategy.
- During the review process, documents are coded or tagged to categorize them. Each review team has their own system, but it’s critical that everyone knows the system. For example, documents may be tagged as privileged (attorney-client privilege), irrelevant, relevant, further review needed etc. The documents are also numbered, which helps identify them later.
- It’s also common practice to have some quality control measures in place to help ensure reviewers are tagging correctly.
Production
- The review process results in a final set of documents that have been determined to be relevant to the case. Production means to “produce” the final set of documents to the opposing party.
- Before the documents are exported both parties will agree on a production format. Formats can include native, near-native, image (TIFF and PDF) and paper.
- A document in its native format will usually include associated metadata. Near-native may include some metadata, but image and paper will not include any metadata. However, additional files are created containing the metadata and other document information
- A “load file” is often produced and included. A load file helps load and organize all the information within eDiscovery software so that the information can be searched and viewed. It also links documents to their metadata.
- In the past, production involved large sending boxes of paper documents to the opposing party.

Presentation
Conclusion
Develop a strategy and plan for each legal discovery request. It is going to help reduce risks and costs.
Can your organization respond to a legal discovery request quickly? To avoid fines and legal sanctions, organizations need to be able to find relevant ESI quickly and easily.
Leveraging the EDRM framework will help you prepare and meet the deadlines of legal requests. Utilizing eDiscovery solutions will help you to be proactive and ready to respond efficiently, saving you time and money.

Ready to take the next step?

QUiVX understands the unique demands and processes legal professionals require during litigation.
Quick Links
Contact Info
-
Address
3339 Vincent Rd. Pleasant Hill, CA 94523 -
Phone
(925) 478-8222 -
Email
sales@quivxca.com
Copyrights © 2025 | QUiVX eDiscovery | All Rights Reserved.
